SainSmart RFID-RC522 & Pi
My first blog about some hardware hacking I am looking at, this article describes connecting the SainSmart RFID-RC522 module with the Raspberry PI. It refers to work that others have done, please see the references at the end of the blog for the sources of information I have used. However by collecting together these sources and my own additions, this will help others.
The SainSmart RFID-RC522 module works with the Mifare RFID tags and uses the RC522 chip. SainSmart have provided a module that can be used as a RFID Reader Card Proximity Module. The module uses the SPI bus to communicate with a controller. For those using a Raspberry PI it is imoprtant to note module uses 3.3v and is compatible with the voltage inputs on the Raspberry PI.
The Serial Peripheral Interface bus (SPI) bus is a synchronous serial data link which the Raspberry PI supports through its GPIO, the PI supports two slave devices using the CE (Chip enable) pins.
Enable the SPI on the Raspberry PI
As the SPI is not enabled by default you will need to edit the raspi-blacklsit.conf in order to enable the SPI interface; this has been blacklisted as most users are not interested in it according to the comment in the file. There are only two devices in the file, the SPI and I2C.
sudo vi /etc/modprobe.d/raspi-blacklist.conf
Add '#' in front of the line spi-bcm2708 to comment it out of the blacklist. Save the file, and you will need to reboot the Raspberry PI, after which the lsmod command should show the spi device (spi_bcm2708) enabled.
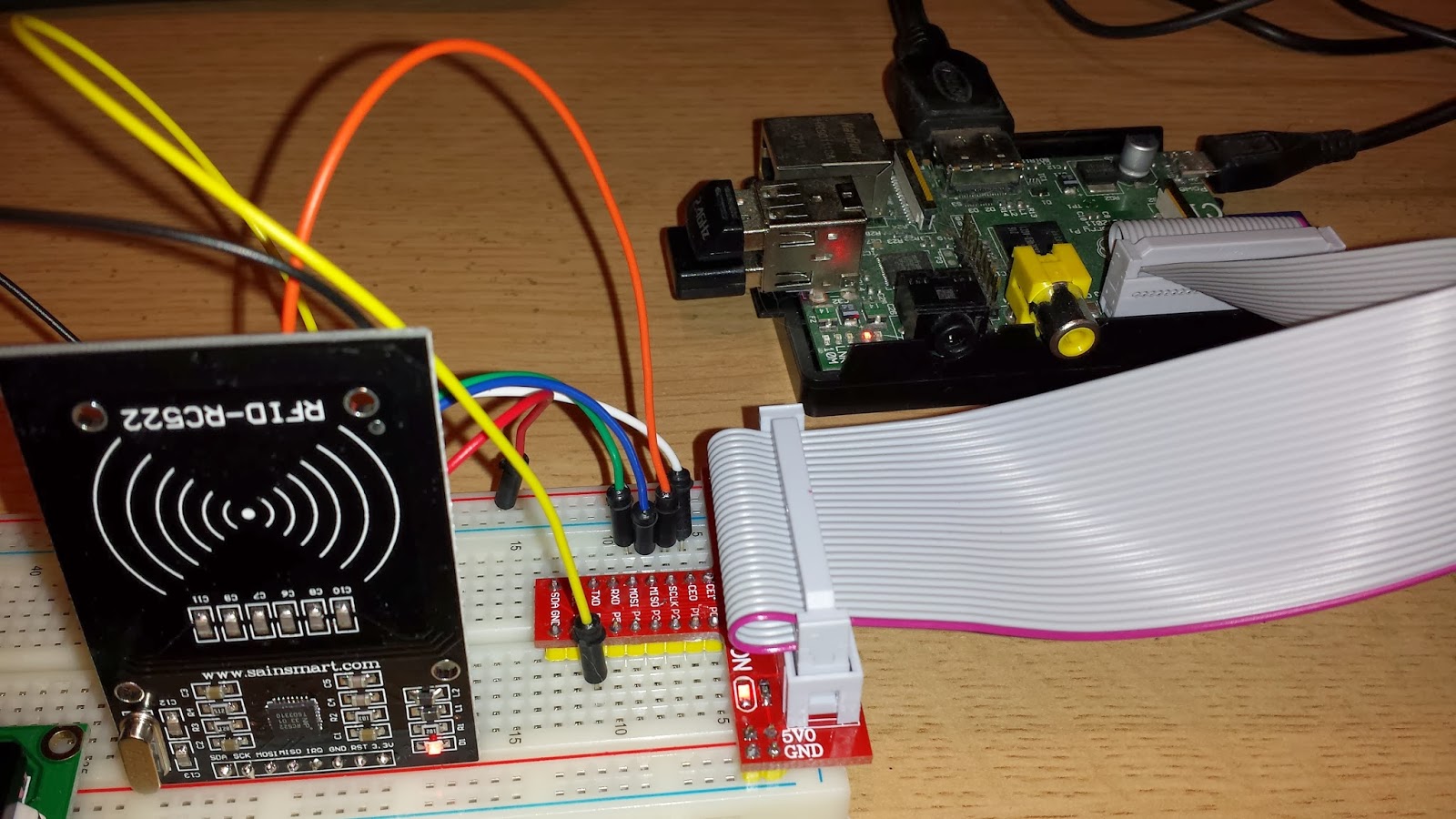
Connection Diagram
Connecting the module to the PI is reasonably straight forward, as the wiring diagram shows, my breadboard set is also pictured.
SPI Code
To use the module from Python, need to load a SPI wrapper, however we need to install ‘python-dev’ to enable us to install the SPI wrapper.
To install ‘python-dev’ :
sudo apt-get install python-dev
In order to read data from the SPI bus in Python we need a set of routines, a suitable set is SPI-Py, available form github.
To do the install, clone the SPI-Py git repository. This is the source code for the SPI python library we’ll be using.
git clone https://github.com/lthiery/SPI-Py.git
Install the SPI-Py module by typing
cd SPI-Py
sudo python setup.py install
Sample Program
In order to test the module out they is a sample code which is a Python port of the example code for the NFC module MF522-AN and provides a small class object to interface with Moduleon the Raspberry Pi.
This is a Python port of the example code for the NFC module MF522-AN
sudo python MFRC522.py
If everything I working you should be able to read the tags that came with the SainSmart module.
Resources
http://www.sainsmart.com/sainsmart-mifare-rc522-card-read-antenna-rf-rfid-reader-ic-card-proximity-module.html
https://github.com/lthiery/SPI-Py
https://github.com/mxgxw/MFRC522-python